Some people consider the Dark Web and Deep Web the same thing. But both of them have a lot of difference. An estimated Deep Web volume is 5 times more than the World Wide Web we have access to. It is sometimes known as the iceberg flowing into the ocean, which is the uppermost part of the Web or Surface Web, and the Deep-water Web is part of the water. You can learn in this article that difference between dark web and deep web.
Establishment of World Wide Web:
Who is not aware of Tim Berners-Lee? This product was associated with “CERN” in 1980, which is responsible for running the world’s largest chemical physician laboratory. While working in this laboratory, he essentially presented the project for high text (connected to each other). The purpose of the project was to spread the latest information for each other. A few months later, after working in the sorbet, Tim Berners-Lee Join a private company where he wanted to know about computer networks. The product was once again rebuilt in 1984, and the “CERN” Europe’s largest computer network became from 1989. Talking about this, Tim Berners-Lee says, “I understand the Hyper Text with only Transmission Control Protocol (TCP) and domain cinema. As a result, there is a broad-scale web-creation web. The main reason for doing was disappointed because when I was working on the head, it was very difficult without this situation. Most technologies used in web-forming such as hypertext, internet, and ability to write text in multiple fonts were already made. I just had to combine them together.
On August 6, 1991, Tim Berners-Lee World Wide Web brought regular scenes. Then the World Wide Web developed “tablet” at the time in coming. Millions of websites have been online in a few years. Nate started new services and life moved on a new trap. The World Wide Web acquired a favorableity on humanity and the world switched into a computer screen. His surprises were visible around the world and in our everyday activities the Internet and especially the World Wide Web’s short time went on increasing. Posts for high-speed links were taken from emails and the main official documents that were buried in official office wardrobes, started digitalizing.
(TOR) Project:
As we previously mentioned, the history of spy on the Internet is as old as the Internet itself. The U.S. Government had its feeling of feelings (perhaps because they were involved in this work) that a system is needed to monitor the data conversion on the Internet. These systems wanted to save their data and communications from the rest of the world. For this purpose three US Naval Research Laboratory employees, one of which were mathematics and two computer scientists, presented onion routing systems. This is the middle of the 90s. The foundation of this system was the same as David Cham, in which he had designed the way to avoid the electronic surveillance or surveillance of the email.
In September 2002 this project was released as TOR Or The Onion Routing. But revolutionary change came when the Naval Research Laboratory in 2004 opened this project open source.
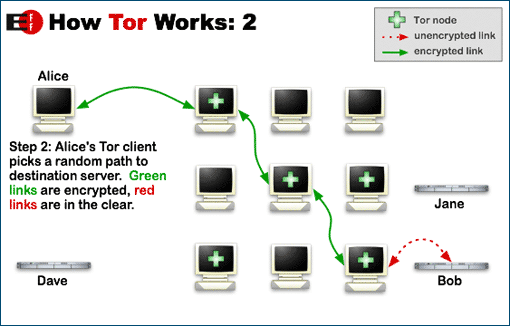
The onion routing process is very interesting. It does not have direct contact between sending and receiving data, but data are delivered to destination destination by relay computers spread across the globe, which are called node or router. It is encrypted three times before sending data or say that three layers of incubation are applied like onion chilies. This data packet is then randomly selected to the selected nodes. This list of nodes provides a special node called “Directory Node”.
A layer of discharge is removed when passing through each router or node. When decrypt the node data, he finds out what the data packet needs to send it forward, but he does not know if the node had given it the data packet it was the first node or the third. After passing all three nodes, the data packet reaches the exit node, where it has been completely decrypted. From there, this data packet is delivered to its destination.
In December 2006 some people jointly formed an organization called The Tor Project, which raised the TOR improvement. The organization was financially supported by Google, Human Rights Watch, and University of Cambridge.
TOR project shakes the foundations of Internet censorship and electronic surveillance. The government, which has been as fertile till the east to west, has tried to close some of the Internet’s doors on their convictions or spying them. Both of these tasks were not possible due to TOR. Edward Snowden’s stolen CIA’s secret instructions shows how irritable of CIA TOR because it was not due to spying and monitoring.
The Dark Web:
The system, which was made to protect people, was also used for a very dangerous task. The law enforcement agencies are the only source of crime on the Internet to reach the crime criminals on the internet. TOR completely removes these marks. Therefore, it is extremely difficult to reach a criminal who uses TOR. Taking advantage of the same thing, criminals have started using TOR for crime. The part of the Internet that you need for TOR to become a crime point, calls the Dark Web.
The Dark Web, World Wide Web is a whirlpool where all kinds of drugs, including herbs, heroin, can be purchased, can be kidnapped, someone can kill for the killer, fake passports can be sold, Theft cards can be purchased, all types of weapons can be purchased. Indeed, every crime that you can imagine, what is going on on the Dark Web.
Dark Web access is not a common URL but also a special type of URL, which is the extension of .onion rather than extension like .com or .net and it is especially difficult to remember. For example Http://3vlqpcqpjlhmd5r5.onion. These addresses find out about underground ground and other dark websites. The search engines do not get scattered near them, so only a small number of people find them.[adsense]
It is difficult for law enforcement agencies that anyone who has a little technical information and is aware of the use of TOR, can sit in any corner of the world in a few minutes to do their own web site and anyone There is no news from the ear. The TOR project has made this work very easy. Many other ready-to-use type tools, including TOR browsers, can be downloaded from their website, which help keep the user’s online identity completely. These websites cannot be found where they are hosted, who is running them. The limit is that the police also finds out about the websites when their crimes are increasing.
The Silk Road was a good example of the Dark Web. There is probably no type of drug on this website that can be purchased. This website was so popular and engaging in illegal fogs that the American FBI had to push the peak peak to close it. Shortly before, access to Silk Road servers was successful and it was closed. But only a few months later, Silk Road 2 came to normal because the Silk Road maker made its source code published on another dark website. At the time the Silk Road was closed, there were several million dollars worth of worth, which the US government occupied.
There are hundreds of websites such as Silk Road on the Web Web, where illegal and sometimes weird services are provided. We also have a dark website where a person living in Europe can be ordered to kill and work is worth only 20 thousand euros. In the case of a journalist, this amount will be 65 thousand euros, while assuming a prominent government official, the value of the officer’s life is one million euros.
On one such website, men, women and children kidnapped for medical experiments are provided. Those medical experiences that cannot be thought in common, resulting in the death of a man, if he dies, he also has the management of his body. God knows how much truth and how much it is, but promises of such kindless service are provided on the Dark Web.
Theft credit card selling business is one of the most popular crimes on the Dark Web. Here a stolen credit card sells five to one hundred dollars per credit card. While using these credit cards is usually used by TOR so that the user cannot identify.
Money taken for criminal offenses for crimes and offense in ordinary life is an important role. Law enforcement agencies are suddenly caught with a large amount of money or purchasing a sudden amount of money in a person’s account. But the situation on the Web Web is different. There is no money in the dollar, euro or any other currency. Because in such case it will be very easy to get to the criminal.
Bitcoin is a big hand in making a crime of the Dark Web. It is the currency that has no physical origin. Nobody prints it, nor can he control it. It is a thing outside the banking system and its value is determined by the difference of demand. This system is very complex and monitoring is extremely difficult. The identification of the sender and the recipient is completely hidden, which makes an idle currency to get money instead of the crime.
Almost all the payouts on the Dark Web are in Bitcoin. Since Bitcoin do not have to be made to change the physical currency like dollars or euros. There are several bit exchange exchanges for those who buy button corners in minutes and throws the original amount to the seller. That’s why nobody has any problem with getting bit coin.
It’s impossible to get rid of the Dark Web in the near future. You might think why not TOR be banned. First, it is not possible because TOR is the knife that was made for vegetable cutting and now if it is being used as a device killer, it does not have a TOR badge, other than the other TOR operating in the same project. Are there If the Web Web is live today with TOR, tomorrow it will get any more support.
We all have the right to use the Internet freely, but it is still right to recognize this right. It is hoped that powerful governments will leave the process of surveillance, it is raw. Such a lot of importance in the project like TOR increases. But the way the Dark Web project has been used is extremely painful.