Threat intelligence tools sit in a difficult place in most security teams. Everyone agrees they are necessary. But few agree on what they are actually for. Fewer still can explain, without drifting into vendor language, how they fit into day-to-day defensive work.
This gap matters. When tools are bought on promise rather than pressure, they quietly fail. Feeds pile up. Dashboards glow. Analysts still chase alerts without context. The organisation feels no safer, just busier.
This blog looks at threat intelligence tools as they are used in real environments. Not as a category on a procurement spreadsheet, but as systems that either sharpen judgement or drown it.
What Threat Intelligence Tools Are Really Meant to do
Threat intelligence tools are not there to tell you that threats exist. You already know that. They are meant to narrow uncertainty at the moment a decision has to be made.
An analyst stares at an IP address. Is it noise, misconfiguration or something worth escalating? A threat intelligence tool should reduce the guesswork. Not eliminate it but reduce it enough to move forward with confidence.
In practice, this means correlating weak signals. External indicators. Internal telemetry. Behaviour over time. When the tool does this well, the analyst spends less time proving a problem exists and more time deciding what to do about it.
When it does not, intelligence becomes decoration. Useful in reports. Useless in incidents.
The Uncomfortable Reality of Most Deployments
Many organisations own threat intelligence tools they barely use. It doesn’t say anything about the tools. It is because they were dropped into environments that were not ready for them.
If logging is inconsistent, intelligence has nothing to attach to. If incident response is slow, intelligence arrives too late to matter. If teams are understaffed, context becomes another item in the queue.
There is also a cultural issue. Intelligence requires trust. Analysts must believe that what they are seeing has been filtered with care. Once false positives dominate, that trust erodes fast. The tool becomes background noise, checked only when someone asks for justification after the fact.
This is where theory and practice part ways.
Types Of Threat Intelligence Tools and Where They Actually Help
Not all threat intelligence tools try to do the same job, even if marketing material suggests otherwise.
Some focus on indicator aggregation. IPs, domains, hashes. These can be useful, but only when enrichment is strong and freshness is clear. An old indicator is often worse than none.
Other tools lean towards tactical context. Mapping activity to known adversary behaviour, often aligned to frameworks such as MITRE ATT&CK. This can help analysts understand intent, not just activity. It works best when paired with strong detection engineering.
There are also tools aimed at strategic intelligence. These look outward. Geopolitical shifts. Industry targeting. Campaign tracking. They matter more to leadership than to a SOC console, but they influence resourcing and risk appetite in subtle ways.
The mistake is expecting one tool to cover all of this equally well.
Where Intelligence Meets Operations
The real value of threat intelligence tools appears when they are woven into operational workflows.
During triage, enrichment should be automatic. Analysts should not be copying indicators into half a dozen portals. If intelligence requires manual effort to access, it will be skipped under pressure.
During investigation, intelligence should explain patterns. Not just that a domain is malicious, but why it exists and how it has been used before. This shortens dwell time and reduces over escalation.
During response, intelligence should inform containment. Blocking infrastructure that an actor consistently reuses is more effective than reacting to each indicator in isolation.
This is quiet work. When it is done well, no one notices. Incidents feel contained and decisions feel calm.
Intelligence Flow
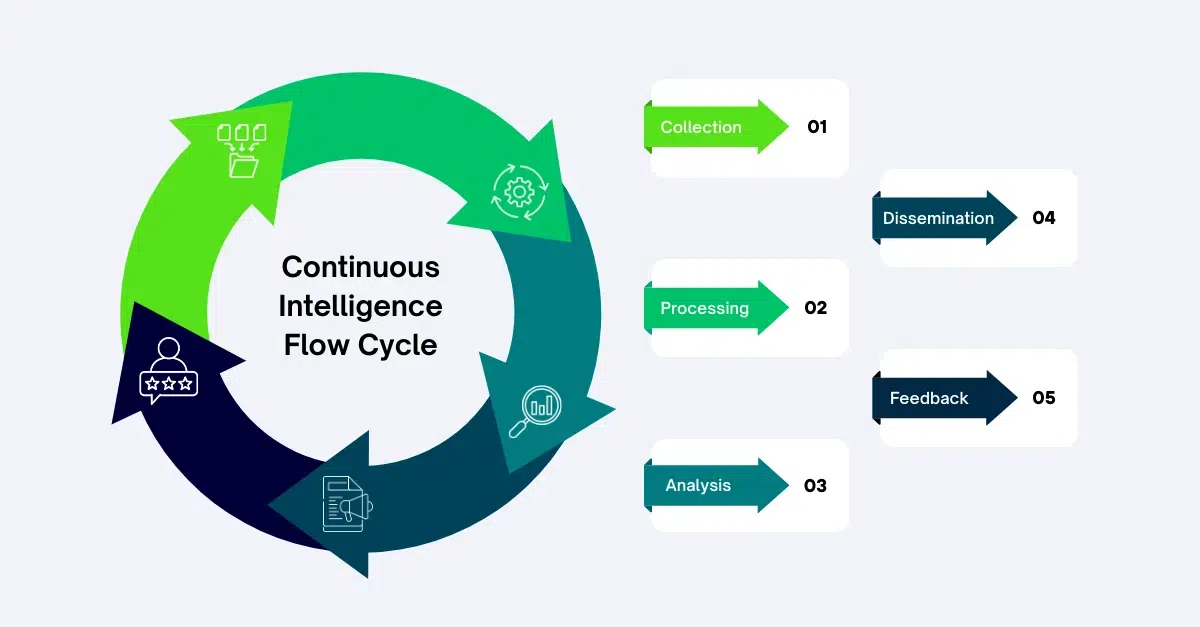
Below is the practical flow cycle through which threat intelligence usually moves:
- Collection
Intelligence arrives from feeds, partners, internal telemetry, and past incidents. Volume is high. Value is unknown.
- Processing
Data is normalised, scored, and stripped of obvious noise. This is where many tools quietly fail or succeed.
- Analysis
Human judgement enters. Patterns are recognised. Hypotheses are formed. Context grows.
- Dissemination
Intelligence is delivered to the point of need. Alerts, dashboards, reports. Timing matters more than format.
- Feedback
Outcomes are fed back into the system. False positives are noted. Gaps are exposed.
Without this feedback loop, threat intelligence tools drift out of alignment with reality.
Integration is the Hidden Cost
Threat intelligence tools do not stand alone. They touch SIEMs, EDR platforms, ticketing systems and sometimes automation layers.
Each integration introduces friction. APIs break. Data models clash. Latency creeps in. These issues are rarely visible during a proof of concept. They surface months later, during real incidents.
Teams that plan for this do better. They assign ownership. They review integrations after incidents. They accept that intelligence quality degrades unless maintained.
Ignoring this reality leads to brittle systems that look impressive until pressure hits.
Measuring Value Without Pretending to be Precise
Security teams often struggle to justify threat intelligence tools because value is indirect. You cannot easily measure incidents that did not happen.
What you can observe is decision quality. Fewer unnecessary escalations. Clearer communication with leadership during incidents.
Over time, patterns emerge. Analysts trust the intelligence. Playbooks reference it naturally. Reports stop explaining basic context because it is already shared understanding.
These are soft signals, but they are real.
The Human Factor That Tools Cannot Replace
No threat intelligence tool replaces experience. It amplifies it.
Junior analysts benefit most when intelligence explains reasoning, not just verdicts. Senior analysts benefit when intelligence removes busywork and surfaces nuance.
Organisations that treat intelligence as a product miss this. It is a practice, supported by tools and shaped by people.
When teams rotate frequently or outsource without continuity, intelligence quality drops. The tool remains, but the context and understanding fades.
Conclusion
Threat intelligence tools are neither silver bullets nor optional extras. Used well, they make security teams calmer and more decisive. Used poorly, they become expensive noise generators.
The difference is rarely the vendor. It is the way intelligence is integrated into operations and maintained over time.
This is where experience matters. Organisations that have seen multiple incident cycles understand what intelligence needs to look like when it counts.
CyberNX can help you here as they offer a comprehensive threat intelligence feed. It provides your organisation with real-time insights into emerging threats, vulnerabilities and attack trends. The goal is not more data. It is better decisions, made under pressure, with fewer surprises.
When intelligence supports that, it earns its place.




